Key Takeaways
- Good UX makes security easy and helps people avoid mistakes.
- Clear, simple designs guide users to stay safe online naturally.
- Trust signs and easy logins make users feel more secure.
- Smart, flexible systems protect everyone without adding extra steps.
- When UX and security teams work together, safety feels effortless.
Fortresses don’t always fall to hackers, sometimes, they crumble from poor design. That’s why understanding how UX design can improve cybersecurity is a necessity for every digital experience. When users face confusing logins or unclear alerts, they unknowingly create risks that strong firewalls alone can’t fix.
Today’s threat landscape demands more than strong passwords and firewalls, it calls for empathy-driven interfaces that guide users toward safer choices. A well-crafted UX doesn’t just make systems easier to use, it makes them harder to abuse.
From reducing phishing risks to boosting MFA adoption, smart UX design strengthens security and turns users into active defenders. Keep reading to uncover how design choices can make security effortless and human-centered.
Why UX Design and Cybersecurity Must Work Together
Cybersecurity has long focused on technical defenses such as encryption, firewalls, and intrusion detection, but most breaches still trace back to human error. According to IBM’s 2024 Cybersecurity Report, nearly 95% of data breaches involve a human factor, often triggered by confusing workflows or poorly designed interfaces.
This is where UX design becomes a critical layer of defense rather than just an aesthetic concern. When security features are difficult to use, users bypass them, choosing convenience over protection. A cluttered dashboard, unclear password prompts, or overly complex authentication can all push users to unsafe shortcuts.
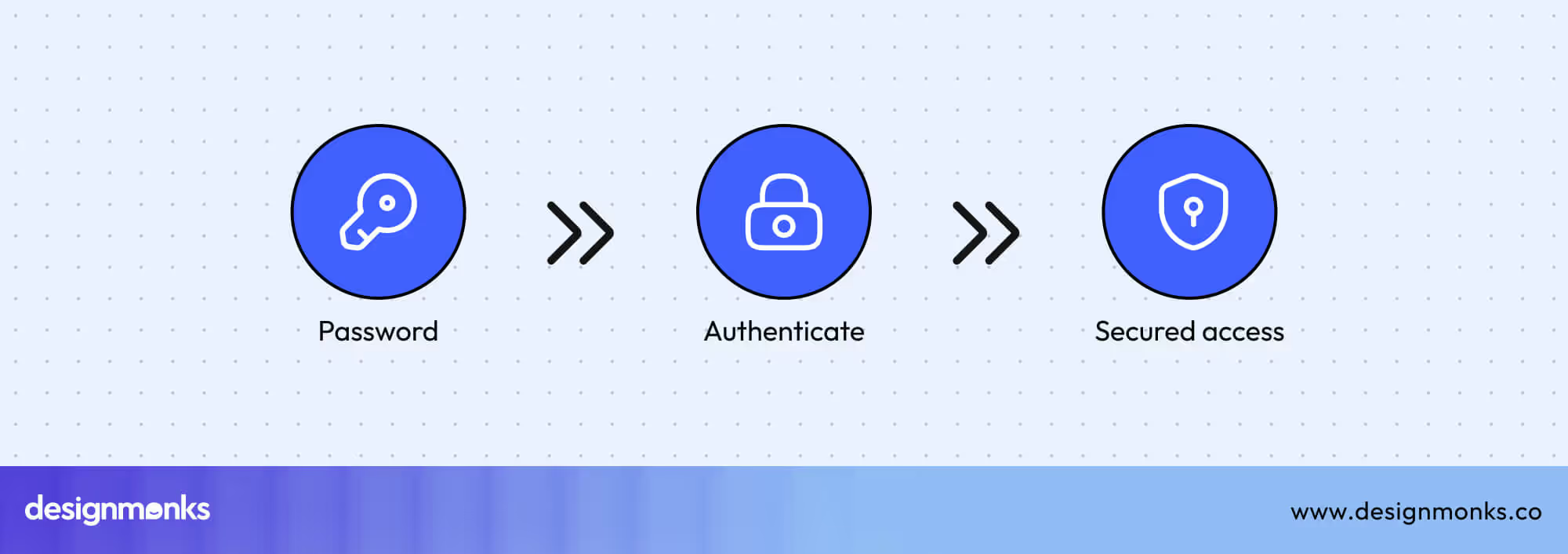
In contrast, intuitive interfaces and clear feedback loops improve adoption of Multi-Factor Authentication (MFA) and reduce accidental exposures. Good UX not only prevents mistakes but also encourages compliance by making secure behavior the easiest option.
Neglecting UX introduces friction that undermines even the strongest systems, eroding user trust in security. By embedding usability in cyber defense, organizations ensure that protection feels natural, not forced.
A secure system that frustrates its users is only half-secure, true resilience comes from merging cybersecurity engineering with user-centric security design that empowers people as the first line of defense.
Key UX Principles that Support Cybersecurity
Cybersecurity isn’t just a technical layer, it’s an experience that must feel intuitive, trustworthy, and effortless. A well-designed cybersecurity interface can prevent errors, guide secure choices, and turn complex security measures into natural user behavior. These core UX principles make that possible:
1. Usability and “Secure by Design”
Building secure-by-design systems means integrating protection into every design decision rather than adding it later. When usability aligns with security, like auto-enabled MFA, default encryption, and session timeouts, users are naturally guided toward safer behavior.

According to the National Institute of Standards and Technology (NIST), 85% of data breaches involve human error, often due to poorly designed interfaces. Secure defaults minimize these risks by ensuring safety doesn’t depend on user vigilance, it’s simply built in.
2. Transparency, Trust & Signaled Security
People trust what they understand. Simple messages like “Your data is encrypted,” clear lock icons, and quick feedback (“Login successful, MFA verified”) help users feel confident and safe.
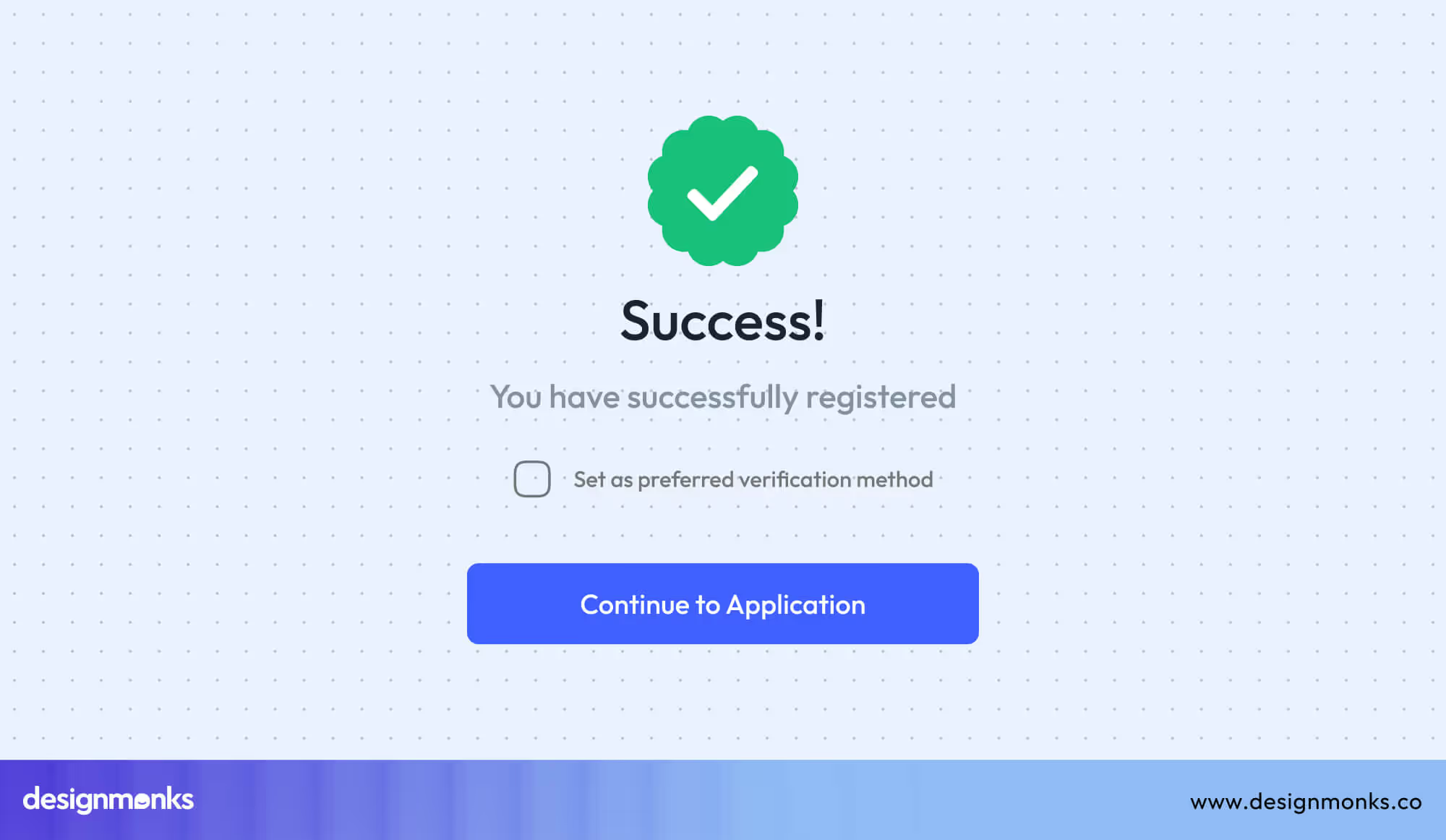
This clarity creates user trust in security and encourages adoption of safe practices. A study by Google’s Security UX Team found that users are twice as likely to complete secure workflows when trust signals are visible and jargon-free.
3. Minimizing User Effort
Too much friction leads users to bypass security, for instance, reusing weak passwords or disabling MFA. Thoughtful UX reduces this tension through biometric authentication UX, password-less sign-ins, or contextual MFA that adapts to user behavior.
These intuitive authentication flow designs balance convenience and safety, ensuring users stay secure without added frustration. Research by Microsoft Identity Division shows that frictionless logins can increase MFA adoption rates by up to 40%, proving that usability directly strengthens cybersecurity.
4. Context-Aware and Adaptive Security
Modern UX design supports adaptive security, which adjusts protection levels based on user context and behavior. Instead of applying the same strict steps to every login, adaptive systems use behavioural analytics to understand what’s normal for each user.
For example, users' regular login device, location, or login time. Or signing in from your regular laptop at home might only need a fingerprint, while an unusual login from another country could trigger multi-factor authentication (MFA) or a one-time code.
This “smart security” approach reduces frustration for legitimate users while catching suspicious activity early. It balances convenience and protection, proving that security doesn’t always have to slow people down. It just needs to be context-aware and user-centric.
5. Accessibility and Inclusive Design
Security should work for everyone, not just tech-savvy users. Many people struggle with complex login steps, unreadable captchas, or unclear error messages. Inclusive UX ensures that data privacy and protection tools are accessible to users with disabilities, language barriers, or limited digital experience.
This means using clear text, visual contrast, voice input compatibility, and screen-reader-friendly elements so all users can complete secure tasks confidently. Accessible security isn’t only ethical, it’s also strategic.
According to the Web Accessibility Initiative, inclusive design improves trust and engagement across all users, helping organizations build broader confidence in their cybersecurity systems.
6. Helpful Error Messages and Recovery Options
Mistakes are part of human behavior, and security design must account for that. Instead of scaring users with harsh error alerts (“Access denied!”), Effective UX provides calm, guiding messages that help people recover safely.
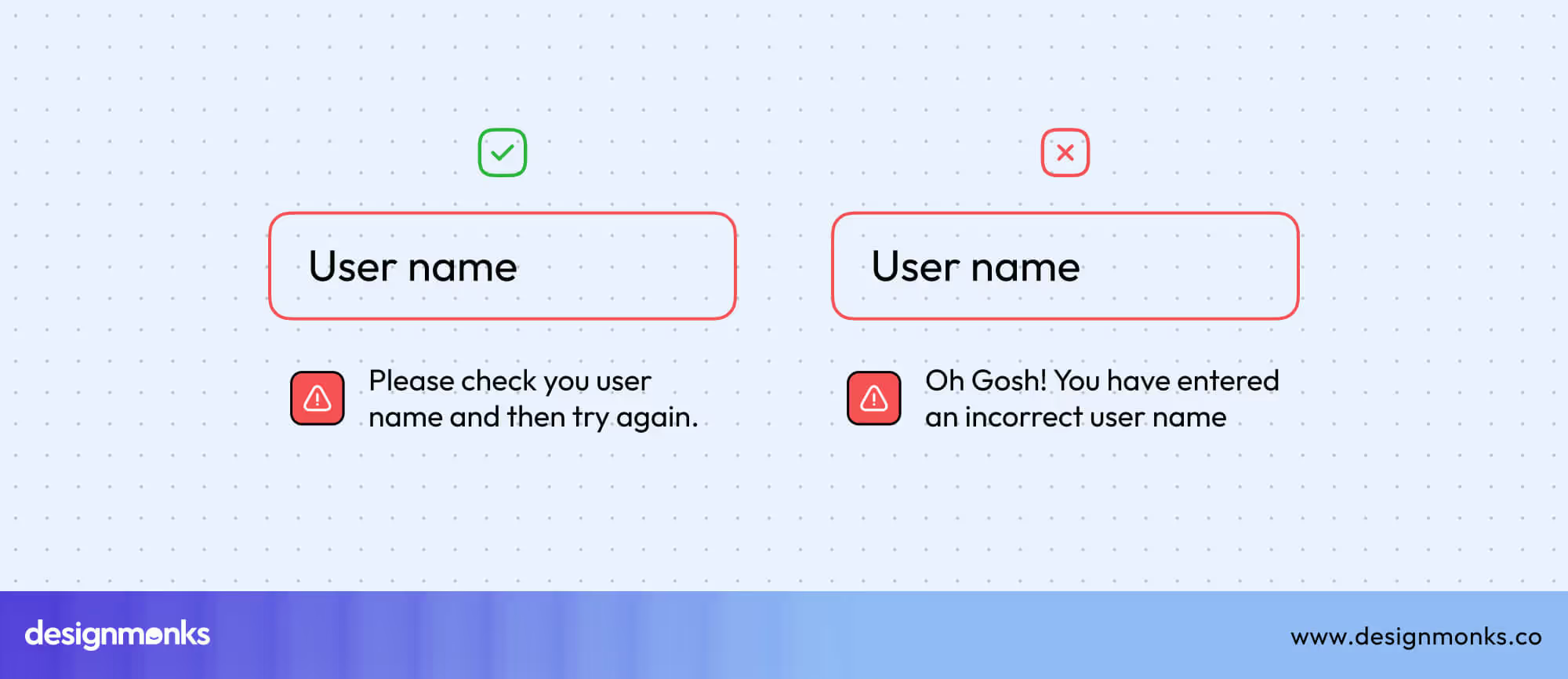
For instance, if someone enters the wrong password, the system might say, “Check your caps lock” or “Try resetting your password securely.” Or if a suspicious link is clicked, a gentle warning, “This site may not be safe. Would you like to go back?” helps users understand and act wisely.
Adding simple, step-by-step recovery options like “verify by phone” or “get help from support” builds user trust and prevents small errors from turning into security breaches. This is the heart of user-centric security design, guiding users toward safety rather than punishing them for mistakes.
UX Design Patterns for Enhancing Cybersecurity
Good UX design can transform cybersecurity from a chore into a seamless habit. By following proven design patterns for security, organizations can strengthen defences while maintaining a frictionless user experience. Let’s explore some critical patterns shaping UX for secure systems today:
1. Authentication Flows: Password-less, Biometric & Contextual MFA
Passwords are no longer the safest or easiest option. Modern systems use password-less logins, biometric authentication (like fingerprints or facial scans), and contextual MFA, which adjusts security based on factors like device type or location.
Behavioural biometrics, such as how a person types or moves the mouse, can verify identity quietly in the background. Companies that use adaptive MFA have seen up to 35% higher login completion rates without reducing security.
Adding simple design elements like progress bars and clear instructions helps users understand each step and lowers the risk of mistakes.
2. Onboarding & Security Education Through UX
Security education should be built into the interface, not left for training sessions. Tooltips, short prompts, and real-time messages can explain why a security step is needed, such as setting up MFA or granting permissions.
For example, a financial company reduced phishing attempts by 40% after adding an onboarding flow that taught users how to spot fake login pages. These small, in-context lessons help people build secure habits naturally.
3. Responsive Feedback & Error-Handling
When something goes wrong in a security process, like a failed login, expired session, or suspicious activity, users need guidance, not confusion. Clear and timely feedback is one of the most important UX patterns for secure systems.
Instead of showing generic messages like “Access Denied” or “Something went wrong,” interfaces should explain what happened and what the user should do next. For example:
- “Your session expired. Please log in again for security.”
- “We detected an unfamiliar device. Please confirm through your registered phone.”
These clear, human-friendly prompts reduce panic and prevent unsafe workarounds, such as users trying to bypass the system. They also help maintain user trust in security systems by showing that protection is active and responsive.
Behind the scenes, security-related errors and alerts can be logged for analysis. This helps UX and security teams identify friction points and improve workflows to prevent repeated issues.
4. Data Minimization & Permission Design
A good data privacy UX means collecting only the information needed to run the service. Transparent permission requests and clear options, such as “Allow access to location only while using the app,” give users control.
Apps that make their permission requests more transparent see up to 25% higher user retention, since people feel safer sharing their data. Respecting privacy not only improves compliance but also builds long-term user trust.
5. Continuous UX Testing for Security
Security design doesn’t stop at launch it evolves through testing and feedback. Continuous UX testing helps teams spot where users struggle, ignore warnings, or make risky mistakes.
Usability tests with security scenarios, like phishing recognition or MFA setup, reveal real behavior and guide improvements before issues become vulnerabilities. Threat modelling for UX also helps predict risky user actions, allowing designers to simplify security steps without reducing safety.
Tracking metrics like MFA adoption or incident reports shows real progress. This ongoing process keeps systems both secure by design and easy to use as threats evolve.
Collaborating with UX and Security Teams from the Start
Security and UX design often run on separate tracks, but they shouldn’t. When both teams work together from the very beginning, products become safer and easier to use. The best results come when threat modelling for UX and journey mapping happen in the same design sprint, blending technical protection with human understanding.
Embedding Security in User Research & Personas
Before any screens are designed, UX researchers should study how people think about security. What confuses users about authentication flows? Why do they skip security steps or mistrust login pages?
Understanding these patterns early helps build systems that are secure by design, combining strong protection with simple, intuitive use. When security needs are baked into personas and user journeys, teams prevent issues instead of patching them later.
Shared Workflows: Threat Modelling Meets Journey Mapping
When UX designers and security analysts collaborate, they can uncover hidden weaknesses in real user paths, such as confusing multi-factor authentication (MFA) steps or unclear error messages.
By reviewing both threat vectors and user pain points together, teams create user-centric secure systems that protect users without frustrating them. This balance improves both security usability and overall trust in the product.
Metrics & KPIs: Measuring UX Impact on Security
To show real progress, teams must measure how usability affects security outcomes. Tracking key metrics helps prove the value of usability in cyber defence:
Tracking these UX–Security KPIs helps teams continuously refine experiences, improve trust, and strengthen protection, proving that good UX is good security.
Sector-Specific Applications and Case Studies
Security UX is not one-size-fits-all. Each sector has unique challenges, requiring customized design solutions that balance usability, compliance, and protection:
FinTech & Banking
Banks and financial apps need to balance strong security with a smooth user experience. Customers expect quick access without complicated steps, but security can’t be compromised.
A Brazilian fintech, Will Bank, implemented a “risk‑based authentication” solution that uses location data and behavioural signals to distinguish between trusted and risky logins. As a result, they reduced fraud losses by ≈ 90% and achieved an ≈ 80% drop in account takeover attempts.

Another case of cybersecurity in Fintech is Shinhan Bank (Korea). They introduced fingerprint login via the FIDO Alliance standard in their Sunny Bank mobile app. This made authentication easier and more trustworthy.
These cases show that clear, adaptive authentication flows and behavioural biometrics can protect users and increase adoption of secure practices.
Healthcare
In healthcare, systems must protect sensitive patient data while remaining accessible to both patients and clinicians. A telehealth provider redesigned its platform with role-based dashboards and adaptive consent prompts, so users only saw the data relevant to their role.
This led to a 22% increase in user satisfaction, and no privacy breaches were reported over six months. By making data privacy clear and simple, healthcare platforms can ensure compliance and build trust without slowing down workflows.
Enterprise SaaS
In B2B SaaS environments, usability doesn’t just benefit end-users, it also helps the teams managing security. Grip Security, a SaaS company specializing in identity risk management, worked with a large enterprise to improve its internal access and off-boarding processes.
Using Grip’s dashboard and workflows, the security team identified over 335 applications in use, which is more than double their initial estimate. They were also able to reduce the manual off-boarding process from weeks to just minutes.
This real-world example shows how intuitive security workflows, user-centric security design, and clear authentication flow design can make internal systems more efficient while strengthening overall cybersecurity.
By simplifying complex processes, SaaS companies can protect sensitive data, reduce human errors, and help security teams respond faster to potential risks.
Emerging Trends: UX, Cybersecurity & AI
The future of cybersecurity UX combines AI, behavioural biometrics, and adaptive interfaces to make systems smarter and easier to use:
Contextual & Adaptive UX
Adaptive UX changes security steps based on the user, device, or situation. For example, frequent logins from a trusted device might skip MFA, while unusual logins require full verification. This keeps security strong without frustrating users.
AI-Powered Security Tools
AI dashboards designed with UX in mind help security teams understand complex threat data quickly. Companies like Palo Alto Networks show that intuitive AI interfaces can cut incident response times by up to 50%.
Behavioural Biometrics & Dark Patterns
Behavioural biometrics, like typing patterns or mouse movements, help verify identity silently and improve security. But misleading or confusing prompts, called dark patterns, can harm trust. An ethical, clear design keeps users confident and engaged in secure practices.
Implementation Roadmap: From Design to Secure Experience
Turning theory into practice requires structure. Here’s a practical roadmap for building user-centric secure systems that unite design and cybersecurity teams:
Step 1: Conduct a UX Audit
Examine every security touchpoint from login screens to alert messages. Identify friction, confusing instructions, or risky shortcuts that could lead to mistakes.
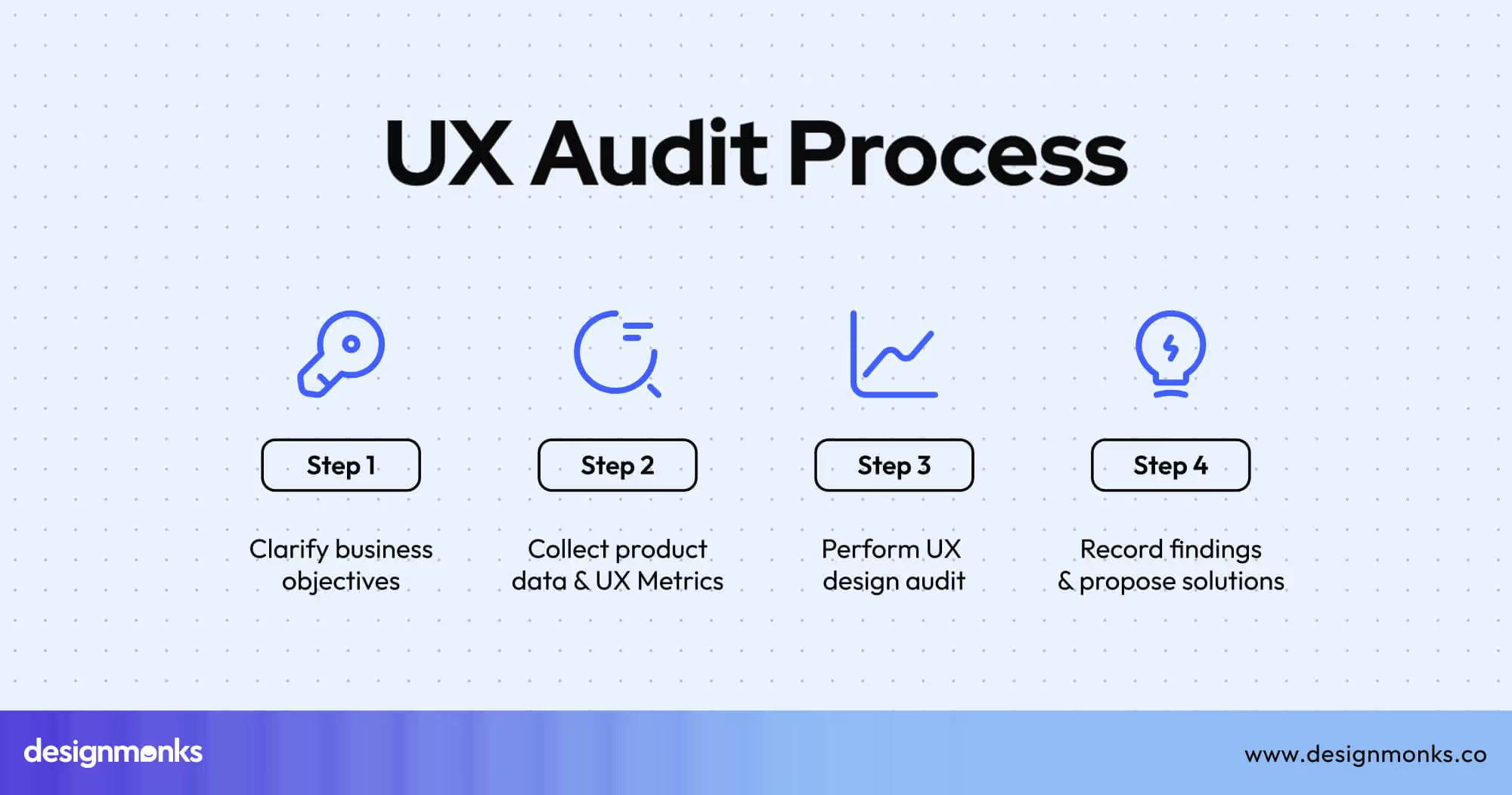
Assess how users interact with MFA, password resets, and permission requests, and note where errors or drop-offs occur. This audit provides a baseline for measurable improvements and highlights immediate usability risks that impact security.
Step 2: Co-Design Sessions
Hold workshops with UX designers, developers, and security experts. Combine threat modelling for UX with user journey mapping to uncover hidden vulnerabilities and align priorities.
Discuss possible attack vectors alongside user pain points and brainstorm solutions that are both secure and intuitive. Early collaboration ensures that security is embedded into the design, rather than added as an afterthought. For further analysis, here are 15 cybersecurity company website examples for inspiration.
Step 3: Prototype, Test & Iterate
Create simple, interactive versions of key security steps like MFA, fingerprint logins, or permission requests. Test them with real users, including exercises like simulated phishing or error scenarios, to see how people actually behave. Use what you learn to improve instructions, error messages, and flow so users make fewer mistakes and feel confident using the system.
Step 4: Launch & Monitor
Roll out the system and track important metrics like MFA usage, security incidents, and user trust. Watch how users interact with security features and gather feedback on confusing parts.
Use this information to make continuous improvements like updating flows, alerts, or guidance as threats, technology, and user behavior change. Secure UX is always evolving, not a one-time project.
FAQs
How does UX design improve cybersecurity?
Good UX design improves cybersecurity with features like MFA, data privacy settings, and password recovery. When people understand and trust the interface, they make fewer mistakes and are more likely to follow secure behaviors, improving cybersecurity overall.
What is “Secure by Design” in UX?
“Secure by Design” means building safety into every part of a product from the start. Instead of adding protection later, it ensures features like encryption, authentication, and session timeouts are already built in, keeping users safe by default.
Why is usability important in cybersecurity?
Usability in cybersecurity is important because if a system is hard to use, people find shortcuts like reusing passwords or skipping MFA. Usability reduces friction and helps users stay compliant with security best practices without frustration.
How can UX designers and cybersecurity teams work together?
UX designers and cybersecurity teams can work together through threat modelling for UX and journey mapping to find weak spots in user behavior. Shared metrics, like MFA adoption rate or error reduction, help both teams measure real improvements in user security.
What are some emerging UX trends in cybersecurity?
Some of the emerging UX trends include behavioural biometrics, adaptive authentication, and AI-driven dashboards that personalize security without adding complexity. These innovations make systems smarter and more user-friendly while strengthening protection.
Conclusion: Designing Security People Can Trust
Knowing how UX design can improve cybersecurity is key to keeping digital systems safe and easy to use. Good design helps people avoid mistakes, use security features like MFA, and trust the system more.
Clear logins, simple alerts, and smart workflows make security feel natural instead of complicated. When usability and protection work together, users become active defenders, and cybersecurity becomes easier, more effective, and part of everyday digital experience.

.svg)





.avif)
.avif)
.avif)
.avif)


.avif)
.avif)
.avif)
.avif)







.avif)